As the world embraces the Smart Nation notion, Critical Information Infrastructures (CIIs) will become increasingly relevant. These CIIs span across aviation, transport, water and energy sectors – and more – and form the basic building blocks of our digital economy.
However, today’s cyber-attacks have expanded beyond the realms of IT (Information Technology) to the physical world of OT (Operating Technology). As industries embrace the acceleration of the digital economy, it has inevitably increased vulnerabilities to cyber threats.
Recent OT Cyber Threats
The interconnected nature of today’s OT infrastructures with digital systems results in an increased attack surface for cyber hackers.
When compared to cyber breaches, OT cyber-attacks pose the same – if not higher – potential for widespread disruption and disastrous consequences. Some of the most recent OT cyber-attacks which hit key facilities in Israel and the United States can attest to this truth.
In this blog post, we will take a look at some of the most recent cybersecurity threats we need to be aware of today:

Israel: Cyber-attacks on water infrastructure in rural areas
In 2020, Israel experienced a series of cyber-attacks targeting its water infrastructure. The attempts at hacking into the control systems were said to modify the country’s water chlorine levels. Moreover, Yigal Unna, Director General of the Israel National Cyber Directorate, said that the attempted cyberattack at water systems in rural Israel marked the first time in modern history. “We can see something like this aiming to cause damage to real life and not to IT or data,” Unna told AP News. Fast forward to the first quarter 2021, another attack on the water infrastructure has occurred.
United States: Ransomware attack on US natural gas pipeline and SolarWinds hack (supply chain attack)
In February 2020, US authorities reported that a ransomware attack on a US natural gas facility resulted in the complete shutdown of a natural gas pipeline for two days. The vector of attack was a malicious link sent to staff at the facility that allowed hackers to gain access to the system and eventually caused the shutdown “of the entire pipeline asset”.
Another cyber incident in December 2020 was reported by the company SolarWinds when malicious code was sneaked into software updates of Orion, which is also owned by the IT firm that monitors the network infrastructures of various businesses and governments for outages.
– – – – – –
Engineering Mindset in OT Cybersecurity
“In many ways, industrial control systems (ICS) cybersecurity is more challenging than simply securing IT environments, because of the fact that OT controls the physical world and they are more often not embedded with security by design,” explained Tan Chin Hua, AVP/Division Manager, ICS Cybersecurity Division Cybersecurity Systems BU at ST Engineering.
“To achieve cyber resilience, OT cyber defenders or teams need to adopt an engineering mindset when it comes to securing industrial control systems, in order to minimise the real-world damage caused by OT cyber-attacks,” he continued.
This means understanding the underlying ICS and SCADA (Supervisory Control & Data Acquisition) systems design which controls the facility, the flow of network traffic, and the vulnerabilities to secure and detect cyber-attacks.
OT Risk Assessment and Monitoring
Very often, vulnerabilities are incubated into ICS due to inadequate policies or network visibility. As we moved beyond OT monitoring and detection, the complexity and the scale of modern ICS networks require constant real-time risk analysis concerning the current threat environment which focuses on specific critical infrastructures.
Understanding OT network risk is also crucial to devise an effective and resilient cybersecurity plan in maintaining the assurance of operations.
Automated and continuous OT risk assessment, monitoring, and management are paramount to protect the OT systems. It allows CISOs to identify and mitigate potential gaps, achieve compliance and optimise their Return on Investment (ROI).

S.A.M. Framework
For OT cybersecurity practitioners, they need to weigh on a whole host of factors when designing their systems. In this regard, the S.A.M. framework provides a useful concept to understand the key factors every OT cybersecurity system should have. S.A.M. stands for:
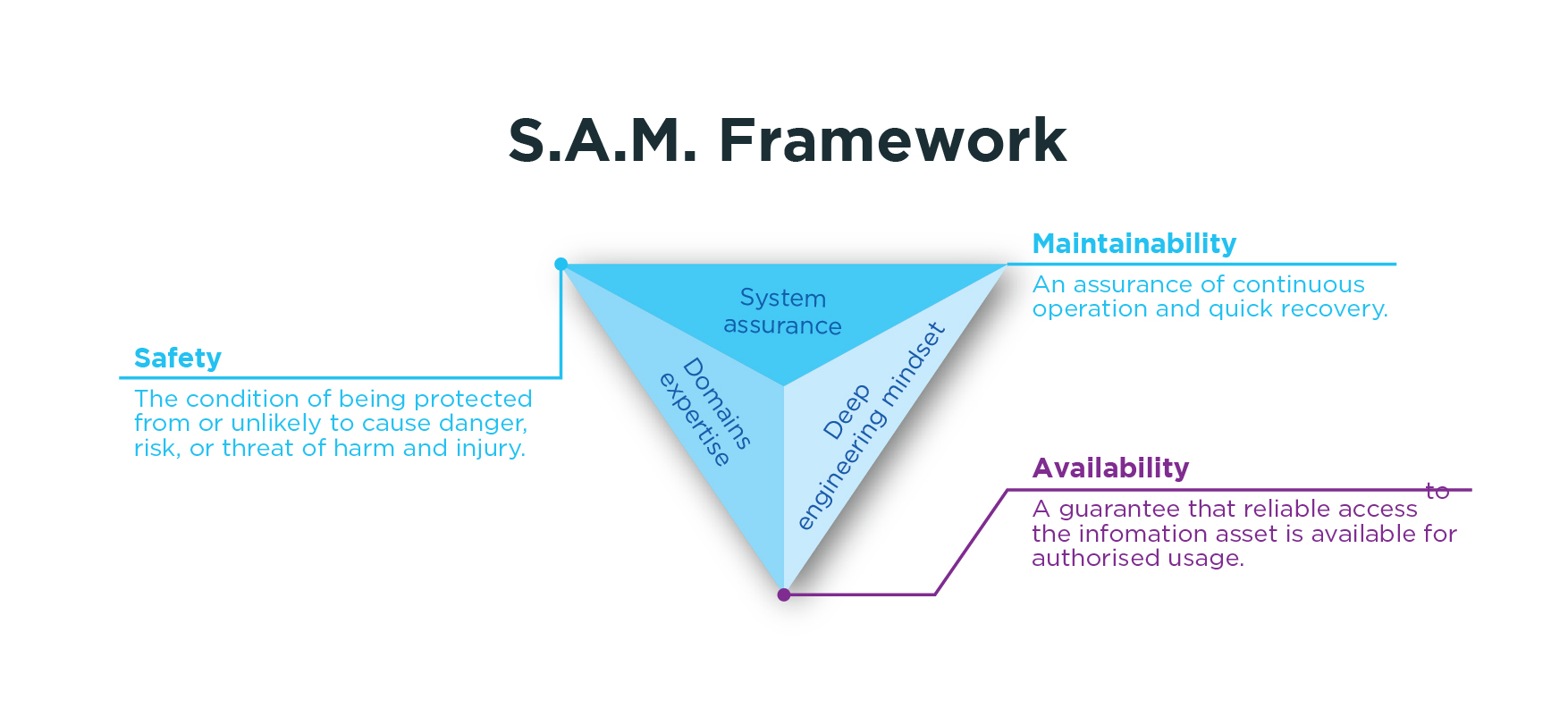
So, what is S.A.M.?
Quite simply, physical infrastructure in the real world is often mission-critical, and they need to operate seamlessly and with high availability, high fault tolerance, and high redundancy.
OT cybersecurity needs to factor in these elements by design – abiding the key criteria of Safety, Maintainability and Availability – which entails engineering expertise that often cuts across multiple disciplines.
Training the Next Generation of OT Cybersecurity Specialists
The spike in cyber-attacks in the OT environment is a cause for concern and calls for a new strategy to train professionals in OT cybersecurity. Even today, OT cybersecurity professionals are facing challenges in securing IT and OT environments, due to the inherent complexity of straddling between both fields.
It is with this in mind that ST Engineering Info-Security has collaborated with Institute of Technical Education (ITE) to launch a new training partnership for ITE students.
Starting January 2021, this collaboration allows us to help students to expand their IT and OT competencies, which furthers our contribution in building the talent pool to support cybersecurity needs in Singapore– growing the cybersecurity human capital.
With ST Engineering’s deep expertise in cyber security and extensive operational experience in the OT domain, we see the importance to ramp up OT cybersecurity competencies.
Conclusion
The threat of OT cyber-attacks is set to increase in the coming years as nations embrace the notion of Smart Nation and with the widespread adoption of Industry 4.0 and IoT devices and connectivity. The connected devices and interconnectivity of networks and systems will continue to rise exponentially. There is a need to prepare for this new landscape, and that means equipping our people with the right Cybersecurity competencies.
Here at ST Engineering, an industry leader with over two decades of cybersecurity experience, our mission is to deliver a holistic suite of trusted OT cybersecurity solutions to help government and ministries, be it for critical infrastructures, or commercial enterprises to stay cyber safe in the accelerated digital economy.
For more information on holistic trusted OT cybersecurity solutions, please visit our website.
Contact us